BitStamp Theft From Old Wallet Addresses is Still Ongoing
Now that it's been over two weeks since the hack you would think that people have received the memo to not use their old BitStamp deposit addresses or at least to not put large sums of bitcoin in them. You would be wrong.
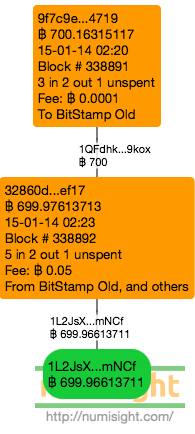
Last Friday there was a 700 BTC deposit that was caught up in the heist. Check out the block numbers and transaction time. It was stolen in the block after it was confirmed in and it was also stolen in 3 minutes flat from the confirmation of the previous transaction. Also, this wasn't an account that has been stolen from before, this the first transaction to the theft wallet for this address.
One obvious question is "was this a customer?" I consider them a Bitstamp customer because they have shared transactions with other affected accounts before. One such transaction is 311f9f which shared inputs with 18dsZT and 1BPezx, both of which were "doners" to the 1J2Ls theft address.
They have been at this address with Bitstamp for over a year now and have made several sizable deposits before.
This transaction is actually relevant for reasons other than its loss. On my podcast I said if I had to make a Vegas bet about what I thought happened I would have gone for some form of server modification in the transaction signing program. I think I would lose money if I ever make that bet since this seems to be conclusive evidence that private keys were lost in the hack, or keys that run a deterministic wallet were leaked and the thief knows what to do with them (which would explain the change address quirk with cold storage). I was hedging my bets because I didn't think such a leakage was necessary for this theft, but now I really see little alternative to that conclusion. Since this transaction occurred over a week since the hack occurred it is unimaginable that the old servers were still running and processing transactions, and the speed of the movement combined with the high fee indicates this isn't a normal transaction. This will likely lead to some very uncomfortable discussions between the customer, Bitstamp, and whoever the customer is accountable to.
Stolen Coins Continue to be Spent
The last time I looked at the outputs I saw only three locations where you could confirm they were being mixed with other coins. Now, the spending is going in earnest all over the place. I considered doing a comprehensive analysis of the particular places they were mixed, but that would take way too many words to write about.
As of block number 339205, which cleared on or about Friday 16 Jan 2015 at 5:33 GMT, a rounded total of 19,940 BTC has been deposited in the 1L2Js theft address. About 95% of those stolen coins have been spent out of that address. For the most part the 5% of the coins remaining represent new balances arriving after the theft went public. For transactions and outputs that are one step away from the theft address a rounded total of 19,274 BTC is either sitting in unspent transaction outputs (60%, or about 11,495) or has been spent in a transaction (40%, or about 7,752). The sum on the first step is greater than the original because some of these transactions involve coins that were not involved in the theft. The second step shows a similar unspent/spent ratio (54%/46%) but a significantly higher rate of mixing with coins outside the theft.
One interesting outbound transaction from the theft involves 1 BTC that has been sent to the Sarutobi iOS game. This is a game that rewarded players with 100 bit donations (just over 2 cents when I was writing this post) if they played the game well. It took a long and winding road, but after 21 transactions Sarutori starts splitting it up into it's hot wallet address 3MXxfN.
All of the transactions not on the top line are 100% derived from the stolen coins, all the way to the very bottom row. And it gets even more insane when you go down some of those chains I didn't expand after Saurtobi split it up into quarters. For these four peel chains, until it hits the users wallet for those transactions, the bitcoins have a 100% taint from the theft address. And those peel chains down the 3MXxfN paths are insanely long, some of the longest peel chains on the blockchain. And those have all been formed in the last three weeks.
Conclusion
Unless something else interesting happens with the Bitstamp theft coins, I don't see myself returning to report on their propagation across the blockchain. There is just too many threads forming from the coins that have been spent and they are for the most part unconnected to each other. I find it unlikely at this point that any of the coins will be returned "intact" to Bitstamp (sorry). The thief has proven that he can unload 40% of them inside of two weeks, so the other 60% may just be bag holders who may or may not be aware of the true origin of their balance.
If you know of any interesting transactions on the blockchain that may benefit from a visual analysis, feel free to drop me a line at danno.ferrin@gmail.com or tweet me at @Numisight and I'll take a look at it. I cannot guarantee blog coverage if I don't find any entertaining findings. I am also open to paid investigations or paid consulting relating to blockchain analysis, and I can be as public or confidential as you desire. For these inquiries please send email to danno@numisight.com.




No comments:
Post a Comment