In March I traveled to Austin to present a paper at the Texas Bitcoin Conference on Bitcoin Transaction Patterns that I discovered while working on my Numisight project. It was a wonderful venue to present at standing on the stage where Austin City Limits is filmed.
TBC, however, has had some issues in getting the contents of their proceedings out. So in the interim I am posting as a PDF the contents of my paper. Enjoy.
Monday, August 3, 2015
Wednesday, May 13, 2015
Millions, Billions, or Trillions?
21 Inc. is the current highest raising Bitcoin startup in the market. But they weren't always "21" because they started out as 21E6, an allusion to the theoretical maximum number of bitcoins from block rewards. Why did they drop the geeky calculator reference to millions? My theory is that it has to do with the fact they aren't slinging bitcoins, but instead millibits. So 21E9 was briefly on the table. But then the VCs caught the vision and realized that one day they would just be slinging bits. And since a bit is on thousandth of a millibit then the name would be a palandromesque 21E12, except I think that many people in bitcoin aren't that good with math and flip signs in strange places, resulting in one thousand bits being a millibit. So I think at this point the marketing people stepped in and realized that some people interested in bitcoin like to gamble (I mean look at how many clones Satoshi Dice spawned!) so they just went with a gambling reference and went with 21. However the motto of "Bitcoin, but with IoT and blackjack!" didn't make it past the nerd culture test because it didn't have the right hook.
CoinDesk Reveals Real Data on 21
While the previous paragraph was entirely satirical CoinDesk did get some real news on 21 via a video that was leaked to them. I won't go over the details of that article and would reccomend you go there to read the news (if you haven't done so already). But embedded in there was a gem: three addresses used in demos posted by 21E6: 1M9ZeS...9x6z, 1hs2xK...Fryy, and 1MaQHC..sd1d. With these three addresses we can ferret out a little bit more information from the blockchain.
The addresses show two very important trails we can follow. First, the privacy sin of a self-spending address is exposed from all three addresses. Second, we see the first of several large sweeps, revealing control of other transaction chains.
If you have any investigations of your own on the blockchain that you would like help with on a paid confidential basis, or would like to learn more about the software I use to help generate these blog posts, or would just like to learn more about bitcoin blockchain forensics please feel free to mail me at danno@numisight.com or at sales@numisight.com.
CoinDesk Reveals Real Data on 21
While the previous paragraph was entirely satirical CoinDesk did get some real news on 21 via a video that was leaked to them. I won't go over the details of that article and would reccomend you go there to read the news (if you haven't done so already). But embedded in there was a gem: three addresses used in demos posted by 21E6: 1M9ZeS...9x6z, 1hs2xK...Fryy, and 1MaQHC..sd1d. With these three addresses we can ferret out a little bit more information from the blockchain.
 |
| Addresses from CoinDesk Article [numisgraph] |
Self Spending Wallet 1A8x13
Whenever I give a public talk I make it clear that re-using addresses is the first and greatest privacy sin. If you want privacy don't reuse your addresses. And if you send your change to the same address you are spending it from, you make analysis such as this absolute child's play. I have no idea why they chose to us a self spending wallet, but this is a major privacy faux pas.
 |
| Peeling Chain of 18Ax13 wallet [numisgraph] |
This wallet was seeded twice from CoinBase (not 21's mining pool). Those are the orange transactions. The peeling chain formed by the wallet feeds into one of four sweeping transactions where we can, via input clustering, presume the contents of other participant peeling chains in the demos. Those are the purple transactions. The yellow transactions are the peeling transactions and the one lone green transaction represents some unspent bitcoins that survived the many VC pitches.
4 large sweeps, one unswept chain
From the other related links, I have identified 5 large peeling chains that fed into this cluster of demos. You can download the fully expanded graph [png][numisgraph] or the graph with the sweeping transactions removed [png][numisgrpah]. These images are too large for me to link into this blogpost with a straight face.
From this we can see that there were about 5 wallets used to perform the various demos, as well as payments directly from CoinBase in some of the demos. Three of the wallets were funded from CoinBase and two of the wallets were funded from two of the sweeps transactions that were previously identified. One of the peeling chains has not been swept, so it is only presumed it was used either in a demo or as part of a QA process right before everyone took the week off for thanksgiving.
These sweep transactions do not, in my opinion, represent multiple wallets on the back end. There are shared addresses between the first and second sweep transaction, and since some of the chains were feed off of these two sweeps it leads me to believe they were recycling bitcoins to be used for the demos, and the third and fourth wallet sweep are from the same wallet. One of the final sweeps actually returned bitcoins to CoinBase as well.
The transactions also tended to clump together in time. However I am hesitant to draw any conclusions about how many VC pitches they did from this demo. Having been in that game before I know that the demo is practiced many times before the first meeting. The video was also showing a canned demonstration of sorts, so the early October clusters were likely the result of multiple practice sessions. And then, when you consider that live demos for pitch meetings can go way off the rails and spawn multiple due diligence meetings then this presumptive analysis without other data (like an executive's travel itinerary) quickly becomes worthless. That being said if I had to go to two or more hands to count the number of VCs they demoed to (not total number of demos, total entities pitched to) then I would be surprised.
These sweep transactions do not, in my opinion, represent multiple wallets on the back end. There are shared addresses between the first and second sweep transaction, and since some of the chains were feed off of these two sweeps it leads me to believe they were recycling bitcoins to be used for the demos, and the third and fourth wallet sweep are from the same wallet. One of the final sweeps actually returned bitcoins to CoinBase as well.
The transactions also tended to clump together in time. However I am hesitant to draw any conclusions about how many VC pitches they did from this demo. Having been in that game before I know that the demo is practiced many times before the first meeting. The video was also showing a canned demonstration of sorts, so the early October clusters were likely the result of multiple practice sessions. And then, when you consider that live demos for pitch meetings can go way off the rails and spawn multiple due diligence meetings then this presumptive analysis without other data (like an executive's travel itinerary) quickly becomes worthless. That being said if I had to go to two or more hands to count the number of VCs they demoed to (not total number of demos, total entities pitched to) then I would be surprised.
Good and Bad OpSec
These transactions show some good and bad OpSec practices on the part 21 Inc. The only real groaner was the re-use of the same address on one of their peel chains. This raised the confidence level that all those sweeps that linked in the other chains really were related to the same set of demos. I also read in the article that each chip was going to come with a hard coded address. I hope they reconsider that and go to an address seed or it's referring to some other internal identifier used by 21 Inc. instead of a literal bitcoin address that will show up on the blockchain. Otherwise we will get side channel attacks opening up by looking at address usage to determine when people are on vacation or other such shenanigans.
OpSec that was neither good nor bad was the peeling chains and sweeping transactions. At this level and with that much transaction volumes there really aren't many good options to conceal these movements. These small TXs would still stick out in a coin tumble and allow for some (by hand) input correlation. And by then the TX fees of a more "professional" service would wipe out the value (we are talking about less than $100 USD here), and similarly the structuring of the TXs would wipe out value in the TX fees. But really what's going to help is more volume and diversity in the services. You won't see that in a demo at a VC pitch, so this is truly unavoidable. Posting the TXIDs in a video (no matter how private) is really what caused this leakage to happen.
But the best OpSec goes to the sourcing of their bitcoins for the demo. I was hoping that they would be using bitcoins they mined themselves, and hence I could send some confirmation data to Neighborhood Pool Watch. But instead they used a very predictable source of coins: CoinBase. For all we know they are selling all of their mined coins through CoinBase. If your source of funds is legal they are one of the best venues to tumble bitcoins strictly based on their volume and legal recognition.
If you have any investigations of your own on the blockchain that you would like help with on a paid confidential basis, or would like to learn more about the software I use to help generate these blog posts, or would just like to learn more about bitcoin blockchain forensics please feel free to mail me at danno@numisight.com or at sales@numisight.com.
Thursday, April 23, 2015
Zombie Coin Movements - The Calbuco Cluster
Over the past two weeks the movement of some "Zombie Coins" has raised some interest in twitter.
A low rumbling source of old bitcoins is erupting causing panic in some traders minds. Kind of like a once dormant volcano suddenly erupting. I dub these coins the "Calbuco Cluster."
Want to play along at home? Download the Numisight Bitcoin Explorer and load the files linked in the captions of the images of this analysis.
Movements of April 2015
Starting on April 15th over 26K BTC moved from a 16 month old address into several new addresses. Over 15K of that value was stored in a single address 1MzG9Gx5G3ZTXtEQT4FJg23Cb3gS6UF982 while the balance was stored in multiple single addresses. About a week later on April 21st the other addresses were moved again in a transaction resulting in one coin of 5K BTC exactly, another one of 5,373 BTC (and one hundred bits) and a leftover address holding only 443 mBTC and change.
None of the addresses used in these movements has been seen before on the blockchain, so no input clustering analysis can be performed.
Mass Movements of Dec 2013
The six transactions that all of these coins originate from are part of a much larger movement of coins that occurred in December of 2013. Spread across 25 transactions all part of the same block (#276158) a total of 103,092.998 BTC shifted from one set of unique addresses to another set of unique addresses. For the most part these were relay transactions (single input and output). The only exceptions were a few addresses that consolidated a little bit of dust spam of 100 bits a piece that had gathered there before the coins moved. I'de post a graph, but that spoils the next section.
What is interesting to note, however, was the market dynamics at the time this movement occurred. The market had just come off of it's record highs a few weeks earlier. Had these coins moved then they would have been worth in excess of USD$100MM, but at the time of the movement they were worth USD$66,615,602.50.
Based on market volume, it is unlikely that this represents a large single trade. At best it represents a position gained over a while and then cashed out in BTC, and that is if they don't represent individual or institutional holdings. However a couple of days before the trade (18 Dec 2013) a large drop in price occurred and there were at least two exchanges (BTC-e and BitStamp) that reported volume that could have accounted for the movements in a single day. But I would have expected the movement to precede the volume given the downside price pressure.
Peel Chain of March 2011
All of these coins that moved in December all originate from a peel chain that occurred in March 2011. Keep scrolling, because it's a long one.
This peel chain, mostly of 150K BTC and possibly from 400BTC, is the origin of all of the coins that moved last week. And this gives us a clue as to how much BTC is left to ooze out.
This chain has origins to a Jan 2011 sweep transaction of 181 smaller coins (not pictured). Values ranged from 40K BTC to 10 mBTC, with most below 1000BTC and clumping at 50BTC. Coins were then relayed and peeled into a 150K BTC and 250K BTC coins. The 250K BTC branch entered a more complex series of transactions and will not be considered part of the cluster.
The 150K BTC branch in early March then proceeded to form a peel chain of 33 peels. 25 of the peels survived until December of 2013 when they were all relayed to new addresses. The other 8 peel coins were spent prior to this event and were not evaluated as part of this analysis.
What Lies Beneath
Of the 25 coin relays in December 2013 only 17 remain unspent, representing 71,714.9987 BTC in the "magma chamber." Note that this weeks and last weeks "eruption" only consisted of 6 of the relay coins. There were also single coin eruptions in September and October of 2014, but since they were smaller and younger coins the "coin days destroyed" graphs didn't register as dramatically.
I honestly have no idea who controls these coins, or how many times they changed hands. The December movement could have been a shuffle to move the keys from a USB key kept underneath someones mattress to bank grade key storage, and it could have easily been someone who had to cover their sales at an exchange days after the trade. The recent movements could have corresponded to an American behind on their taxes paying the piper so to speak, since it did occur on a major US Tax Deadline. But the one thing I am very confident of is that these are not the Mt. Gox coins you've been looking for *Obi-Wan*Jedi*wave*.
FYI: Those #bitcoin days that were destroyed in Apr 16 are now moving again: http://t.co/UFBvyatvUA
— Datavetaren (@Datavetaren) April 22, 2015
A low rumbling source of old bitcoins is erupting causing panic in some traders minds. Kind of like a once dormant volcano suddenly erupting. I dub these coins the "Calbuco Cluster."
Want to play along at home? Download the Numisight Bitcoin Explorer and load the files linked in the captions of the images of this analysis.
Movements of April 2015
Starting on April 15th over 26K BTC moved from a 16 month old address into several new addresses. Over 15K of that value was stored in a single address 1MzG9Gx5G3ZTXtEQT4FJg23Cb3gS6UF982 while the balance was stored in multiple single addresses. About a week later on April 21st the other addresses were moved again in a transaction resulting in one coin of 5K BTC exactly, another one of 5,373 BTC (and one hundred bits) and a leftover address holding only 443 mBTC and change.
None of the addresses used in these movements has been seen before on the blockchain, so no input clustering analysis can be performed.
 |
| April 2015 Movements of the Calbuco Cluster [numisgraph] |
The six transactions that all of these coins originate from are part of a much larger movement of coins that occurred in December of 2013. Spread across 25 transactions all part of the same block (#276158) a total of 103,092.998 BTC shifted from one set of unique addresses to another set of unique addresses. For the most part these were relay transactions (single input and output). The only exceptions were a few addresses that consolidated a little bit of dust spam of 100 bits a piece that had gathered there before the coins moved. I'de post a graph, but that spoils the next section.
What is interesting to note, however, was the market dynamics at the time this movement occurred. The market had just come off of it's record highs a few weeks earlier. Had these coins moved then they would have been worth in excess of USD$100MM, but at the time of the movement they were worth USD$66,615,602.50.
Based on market volume, it is unlikely that this represents a large single trade. At best it represents a position gained over a while and then cashed out in BTC, and that is if they don't represent individual or institutional holdings. However a couple of days before the trade (18 Dec 2013) a large drop in price occurred and there were at least two exchanges (BTC-e and BitStamp) that reported volume that could have accounted for the movements in a single day. But I would have expected the movement to precede the volume given the downside price pressure.
Peel Chain of March 2011
All of these coins that moved in December all originate from a peel chain that occurred in March 2011. Keep scrolling, because it's a long one.
 |
| March 2011 Calbuco Cluster Peel Chain [numisgraph] |
This chain has origins to a Jan 2011 sweep transaction of 181 smaller coins (not pictured). Values ranged from 40K BTC to 10 mBTC, with most below 1000BTC and clumping at 50BTC. Coins were then relayed and peeled into a 150K BTC and 250K BTC coins. The 250K BTC branch entered a more complex series of transactions and will not be considered part of the cluster.
The 150K BTC branch in early March then proceeded to form a peel chain of 33 peels. 25 of the peels survived until December of 2013 when they were all relayed to new addresses. The other 8 peel coins were spent prior to this event and were not evaluated as part of this analysis.
What Lies Beneath
Of the 25 coin relays in December 2013 only 17 remain unspent, representing 71,714.9987 BTC in the "magma chamber." Note that this weeks and last weeks "eruption" only consisted of 6 of the relay coins. There were also single coin eruptions in September and October of 2014, but since they were smaller and younger coins the "coin days destroyed" graphs didn't register as dramatically.
I honestly have no idea who controls these coins, or how many times they changed hands. The December movement could have been a shuffle to move the keys from a USB key kept underneath someones mattress to bank grade key storage, and it could have easily been someone who had to cover their sales at an exchange days after the trade. The recent movements could have corresponded to an American behind on their taxes paying the piper so to speak, since it did occur on a major US Tax Deadline. But the one thing I am very confident of is that these are not the Mt. Gox coins you've been looking for *Obi-Wan*Jedi*wave*.
Tuesday, March 31, 2015
Prosecution Futures - The Blockchain Evidence Against Force and Bridges
I once heard a joke calling bitcoin transactions "prosecution futures," the premise being that any illegal activity you conduct on the blockchain will be sitting there ready for prosecuting agencies to find. The oldest reference to "prosecution futures" I could find in three pages of search results was from the naked capatalist blog. The author imagined that the futures were for money laundering and tax evasion. I don't think it ever crossed their mind that what would ultimately transpire was sworn federal agents violating their oath.
Enter the latest and most surreal twist in the Silk Road saga to date. Yesterday the DOJ released a criminal complaint against former DEA agent Carl Mark Force IV and former Secret Service Agent Shaun Bridges. The surreal part is not the core allegation, where it is alleged that Force and Bridges were skimming the profits from undercover drug sales. But where they had managed to embed themselves so deeply they were engaging in some of the more salacious stories emerging at the trial. The January 2013 theft? That was the undercover agents. One of the murder for hire allegations? Yep, complete with faked pictures. Causing the collapse of Mt. Gox? Well, no. I'm not convinced about it yet but it is at least in the realm of reasonable theories. Even Hollywood couldn't make this up. But remember, these are all allegations until proven in a court of law at trial.
I am not a Lawyer
I would like to point out that I am not a lawyer. I did not do any correspondence courses to the University of American Samoa and it didn't take me three tries to pass the State of New Mexico Bar Exam (I've never tried). So if you are reading this blog realize this is for entertainment purposes and is not legal advice. I feel the need to say this since I'm going to be re-creating some of the exhibits and pointing out a few minor clerical errors.
However what I do find significant in this complaint is that three of the exhibits showed a significant amount of blockchain analysis. This is something we didn't see in the Ross Ulbricht trial, the only connections entered into evidence were direct transactions between the Iceland server and Ross's laptop. But to be honest, that was really all they needed since the evidence was so overwhelming. This case is significant because they are entering in as evidence bitcoin traces involving multiple transactions. (And they even had a footnote on page 9 discussing the proper capitalization of bitcoin.)
Exhibit B
Exhibit B is the most complex graph in the complaint. It outlines a 525 BTC payment to Force received from DPR, where Force pretending to be a corrupt government official offering his knowledge and expertise (except allegedly he wasn't pretending). I was able to recreate this graph by entering only one of the addresses and waling up and down the transaction graph, so despite my nits the exhibit is generally correct.
The transactions where Force was paid by DPR begin at the top four orange transactions. What follows is a series of relays, peels, and sweeps that wind up with one large sweep at the 02d7b4b8 transaction and then a final sweep at f7dcec4f before a relay into CampBX. There are two transactions in the middle of the shuffle representing nearly 34 BTC which was replaced from a transaction in the second sweep that (according to the exhibit graph) match back up to Silk Road. This appears to be what passed for coin shuffling at Silk Road, but to be fair CoinJoin had just been announced during the events in this exhibit. But what made this game of three card Monte pointless was when the whole value was combined in the end just before the deposit into CampBX.
Compared to the Exhibit B graph (on page 55 of the PDF) there is one major stylistic difference is that I focus the vertices of the graphs in this blog on the transactions and the edges represent the transaction outputs that are attached to particular bitcoin addresses. The exhibit graph has the vertices as the transaction outputs. In fact, some vertices represent multiple transactions that are self spending peeling transactions. The flaw I see in this is that there is no room for the transaction IDs and some details about the creation and spending of transaction outputs can be lost.
There are also a few clerical errors in the exhibit in the complaint, and some elided details that exist in the transactions that are lacking in an address focused graph. This is likely the result of copy paste errors as it appears that a tool such as PowerPoint or Analyst's Notebook was used to generate the exhibit. The left two branches from DPR have the second and third addresses swapped. There are some coins that exit the system just to the lower right of the center of the exhibit. Those coins do exit but there are several intervening addresses left out of the exhibit. And the major sweep at the bottom of the graph is actually two sweeps from two different addresses, all winding up in the 136jvwh address eventually.
There are advantages of a hand made graph. The lines and arrangement of the graph are much more aesthetically pleasing. Right now I am using JGraph for my graphing layout but I am exploring a more expensive option, but based on my professional experience yFiles is the best library in the business for graph layouts. You also pay for the quality of the work.
All these nits aside the core narrative of the exhibit is correct: DPR danced 525 bitcoins to Force in a complex series of transactions. The clerical errors and stylistic nits do nothing to diminish this message.
Exhibit E
Exhibit E represents the payment of 770 BTC from DPR to Force (under the pseudonym frenchmaid) in connection with the alleged murder for hire that Force lied about carrying out.
This graph shows a series of five payments relayed to Force that were in the end deposited into one of several CampBX deposit addresses. There were no clerical errors in this page (there were also less addresses). The edge on the left also didn't show the structure of the peeling chain that was formed by breaking off the four payments. Creating four separate amounts did nothing to hide the shared origin of the amounts.
Exhibit F
This exhibit is even less interesting than Exhibit E was compared to Exhibit B. It represents the skimming done by Bridges into Mt. Gox, and then to his Fidelity account.
All of the transactions were peeing transactions, self peeling transactions at that. The single address used at Mt. Gox then received the proceeds which he then cashed out into his Fidelity account. Seriously, his Fidelity account, a large brokerage that was likely more than happy to hand over customer information when served with a legal and correct search warrant.
Conclusion
This will be an interesting case to watch as it winds its way to trial. Whereas the Ross Ulbricht case relied on simple single transactions this case depends on a more complex series of blockchain transactions to prove the allegations against Carl Mark Force IV. When it comes to entering information in as evidence this is likely a case that will be sited in much of the case law that will develop.
You also may have noticed the "numisgraph" links in the captions. If you want to play along at home you can download the public alpha of the Numisight Bitcoin Explorer and load the attached files and explore the related transactions yourself.
Enter the latest and most surreal twist in the Silk Road saga to date. Yesterday the DOJ released a criminal complaint against former DEA agent Carl Mark Force IV and former Secret Service Agent Shaun Bridges. The surreal part is not the core allegation, where it is alleged that Force and Bridges were skimming the profits from undercover drug sales. But where they had managed to embed themselves so deeply they were engaging in some of the more salacious stories emerging at the trial. The January 2013 theft? That was the undercover agents. One of the murder for hire allegations? Yep, complete with faked pictures. Causing the collapse of Mt. Gox? Well, no. I'm not convinced about it yet but it is at least in the realm of reasonable theories. Even Hollywood couldn't make this up. But remember, these are all allegations until proven in a court of law at trial.
I am not a Lawyer
I would like to point out that I am not a lawyer. I did not do any correspondence courses to the University of American Samoa and it didn't take me three tries to pass the State of New Mexico Bar Exam (I've never tried). So if you are reading this blog realize this is for entertainment purposes and is not legal advice. I feel the need to say this since I'm going to be re-creating some of the exhibits and pointing out a few minor clerical errors.
However what I do find significant in this complaint is that three of the exhibits showed a significant amount of blockchain analysis. This is something we didn't see in the Ross Ulbricht trial, the only connections entered into evidence were direct transactions between the Iceland server and Ross's laptop. But to be honest, that was really all they needed since the evidence was so overwhelming. This case is significant because they are entering in as evidence bitcoin traces involving multiple transactions. (And they even had a footnote on page 9 discussing the proper capitalization of bitcoin.)
Exhibit B
Exhibit B is the most complex graph in the complaint. It outlines a 525 BTC payment to Force received from DPR, where Force pretending to be a corrupt government official offering his knowledge and expertise (except allegedly he wasn't pretending). I was able to recreate this graph by entering only one of the addresses and waling up and down the transaction graph, so despite my nits the exhibit is generally correct.
 |
| Exhibit B [numisgraph] |
Compared to the Exhibit B graph (on page 55 of the PDF) there is one major stylistic difference is that I focus the vertices of the graphs in this blog on the transactions and the edges represent the transaction outputs that are attached to particular bitcoin addresses. The exhibit graph has the vertices as the transaction outputs. In fact, some vertices represent multiple transactions that are self spending peeling transactions. The flaw I see in this is that there is no room for the transaction IDs and some details about the creation and spending of transaction outputs can be lost.
There are also a few clerical errors in the exhibit in the complaint, and some elided details that exist in the transactions that are lacking in an address focused graph. This is likely the result of copy paste errors as it appears that a tool such as PowerPoint or Analyst's Notebook was used to generate the exhibit. The left two branches from DPR have the second and third addresses swapped. There are some coins that exit the system just to the lower right of the center of the exhibit. Those coins do exit but there are several intervening addresses left out of the exhibit. And the major sweep at the bottom of the graph is actually two sweeps from two different addresses, all winding up in the 136jvwh address eventually.
There are advantages of a hand made graph. The lines and arrangement of the graph are much more aesthetically pleasing. Right now I am using JGraph for my graphing layout but I am exploring a more expensive option, but based on my professional experience yFiles is the best library in the business for graph layouts. You also pay for the quality of the work.
All these nits aside the core narrative of the exhibit is correct: DPR danced 525 bitcoins to Force in a complex series of transactions. The clerical errors and stylistic nits do nothing to diminish this message.
Exhibit E
Exhibit E represents the payment of 770 BTC from DPR to Force (under the pseudonym frenchmaid) in connection with the alleged murder for hire that Force lied about carrying out.
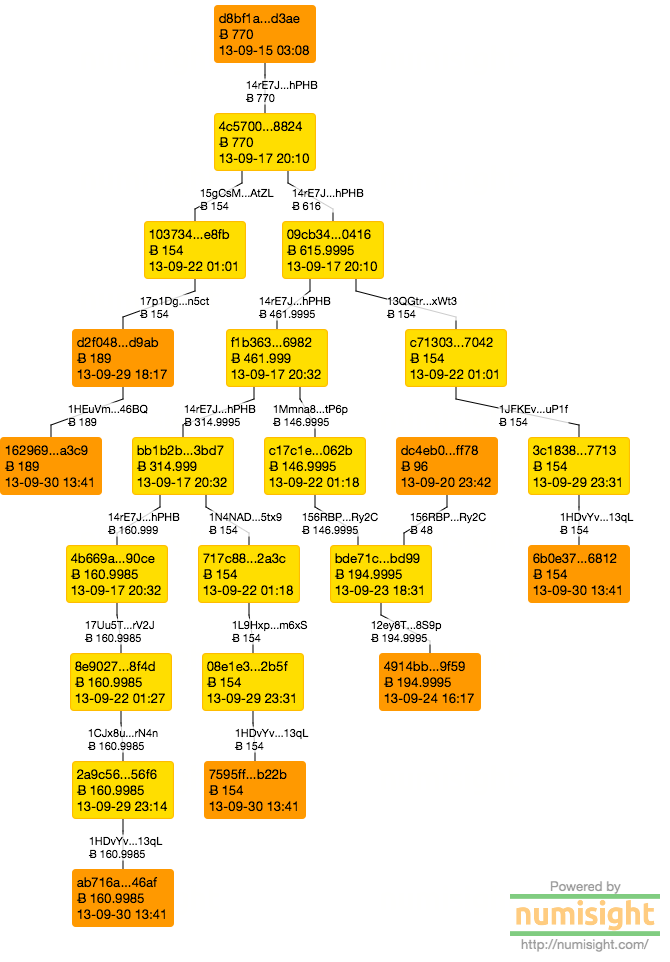 |
| Exhibit E [numisgraph] |
Exhibit F
This exhibit is even less interesting than Exhibit E was compared to Exhibit B. It represents the skimming done by Bridges into Mt. Gox, and then to his Fidelity account.
 |
| Exhibit F [numisgraph] |
Conclusion
This will be an interesting case to watch as it winds its way to trial. Whereas the Ross Ulbricht case relied on simple single transactions this case depends on a more complex series of blockchain transactions to prove the allegations against Carl Mark Force IV. When it comes to entering information in as evidence this is likely a case that will be sited in much of the case law that will develop.
You also may have noticed the "numisgraph" links in the captions. If you want to play along at home you can download the public alpha of the Numisight Bitcoin Explorer and load the attached files and explore the related transactions yourself.
Friday, March 27, 2015
Numisight Bitcoin Explorer Public Alpha Release
Today I am releasing a version of the tool I've been using to create the graphics you see on this website. The Numisight Bitcoin Explorer can be downloaded from the Numisight website.
This version of the software provides the core visualization engine used in the full "Studio" version of the software. The reporting and profile creation tools are not present a they are still under development. You can save and load graphs as well as export as a PNG (with a watermark) any graphs you generate. When loading an old graph please note that coins that were once unspent may now be included in a transaction. The layout may also mutate from the saved graph because of this as the topology may change.
Using the search box you can copy in any address or transaction ID and the resulting transactions will be shown on the main canvas. To expand a transaction you can double click the box, and to expand just the inputs and outputs you can use the context (right click) menu. This menu also allows you to remove unwanted transactions. Be careful however, currently I take no effort to restrict the amount of data that is shown on the canvas. Pay attention to the number of inputs and outputs for each transaction to be sure the graph won't be overwhelming to look at. There is a performance penalty for viewing large numbers of transactions, but usually you will encounter the usability issues of attempting to make sense of a thousand transactions before the performance penalty becomes troublesome.
For data I provide access to two public data sources (there were three, but one of them got out of the Bitcoin API game). Bitpay Insight is the primary data provider, and BlockCypher is available on the configuration tab of the data screen. If you use BlockCypher I recommend you provide your own API Key rather than sharing the bundled key. Currently I only make use of the basic BlockCyper APIs, not any of the unique data sources like their library of double spend data.
The license for this version is of an evaluation license, and this version is licensed until block 400,000 is mined. Currently this is not enforced in the software but that is something I am looking into. If you want a more permissive license feel free to email us and we can work something out.
If you have any questions or problems, please email support. Right now we have a Mac and Windows 64-bit version. I'm working on getting a Linux (Ubuntu) version ready and that should be out within a week. If these don't work for you email support and let us know what versions you may need.
For the next batch of blog posts I will be doing, I intend to release the .numisgraph files so that you can explore the transactions graphs yourself. I may also be providing graph files that are not shown in the blog posts that are used to back up my analytic conclusions but don't add to the primary narrative.
This version of the software provides the core visualization engine used in the full "Studio" version of the software. The reporting and profile creation tools are not present a they are still under development. You can save and load graphs as well as export as a PNG (with a watermark) any graphs you generate. When loading an old graph please note that coins that were once unspent may now be included in a transaction. The layout may also mutate from the saved graph because of this as the topology may change.
Using the search box you can copy in any address or transaction ID and the resulting transactions will be shown on the main canvas. To expand a transaction you can double click the box, and to expand just the inputs and outputs you can use the context (right click) menu. This menu also allows you to remove unwanted transactions. Be careful however, currently I take no effort to restrict the amount of data that is shown on the canvas. Pay attention to the number of inputs and outputs for each transaction to be sure the graph won't be overwhelming to look at. There is a performance penalty for viewing large numbers of transactions, but usually you will encounter the usability issues of attempting to make sense of a thousand transactions before the performance penalty becomes troublesome.
For data I provide access to two public data sources (there were three, but one of them got out of the Bitcoin API game). Bitpay Insight is the primary data provider, and BlockCypher is available on the configuration tab of the data screen. If you use BlockCypher I recommend you provide your own API Key rather than sharing the bundled key. Currently I only make use of the basic BlockCyper APIs, not any of the unique data sources like their library of double spend data.
The license for this version is of an evaluation license, and this version is licensed until block 400,000 is mined. Currently this is not enforced in the software but that is something I am looking into. If you want a more permissive license feel free to email us and we can work something out.
If you have any questions or problems, please email support. Right now we have a Mac and Windows 64-bit version. I'm working on getting a Linux (Ubuntu) version ready and that should be out within a week. If these don't work for you email support and let us know what versions you may need.
For the next batch of blog posts I will be doing, I intend to release the .numisgraph files so that you can explore the transactions graphs yourself. I may also be providing graph files that are not shown in the blog posts that are used to back up my analytic conclusions but don't add to the primary narrative.
Wednesday, March 11, 2015
FBI Silk Road Auction of March 2015
In March 2015 the US Marshals Service (USMS) held their third auction of bitcoins connected with the FBI case against Ross Ulbricht and the first Silk Road market. Bids were submitted blindly on the 4th of March and the USMS moved the bitcoins on the 9th and 10th of March.
According to the auction announcement the funds were required to begin transfer by 2pm EST in Washington DC (which wound up being 1pm since daylight savings time began the day before). Bids were to be "transferred to winning bidders in the order that each winning bid was received." It appears that the winners had all their financial ducks in a row because the transfer of the bitcoins began promptly after the deadline passed.
Winner #1 - itBit
According to CoinDesk the winner of the first lot paid out, to the sum of 3,000BTC, was itBit. Headquartered in New York itBit is a bitcoin exchange that also has a significant office in Singapore.
Starting right after their lunch break the USMS sent a test transaction to the winning address of 50 mBTC. This is a pattern we saw in the second auction and looks to be one they are going to be using going forward. A half hour later the remaining bitcoins were transferred to the winning address. No fees were paid for either of these transactions.
According to the auction announcement the funds were required to begin transfer by 2pm EST in Washington DC (which wound up being 1pm since daylight savings time began the day before). Bids were to be "transferred to winning bidders in the order that each winning bid was received." It appears that the winners had all their financial ducks in a row because the transfer of the bitcoins began promptly after the deadline passed.
Winner #1 - itBit
 |
| Transactions to the first winner of the auction. |
Based on who won these bitcoins and the immediate transactions that occurred it is my theory that the deposit went straight into the itBit operational wallet. The two unspent transactions in this graph would represent a customer withdrawal and a "change address" ready for more use by the operational wallet.
Winner #2 - Unknown
It is currently unknown who won the 20K lot of bitcoins, which represents all of the series A blocks of bitcoin available.
 |
| Transactions to the second winner of the auction. |
The USMS initiated the second winner's transaction about a half an hour after completing the first one. Again they began with a test transaction of 50mBTC and then two hours later completed the rest of the transaction. It is unclear why there was more time for this transaction, representing 14 blocks between transactions rather than the single block for the first winner. They also paid no fees to receive their bitcoin.
There is not much that can be said about this winner, other than they have exercised some excellent "privacy hygiene" when it comes to the transaction information. The address is one that has not been seen on the blockchain prior to the auction, and the only action seen with the purchased amounts is a single sweeping transaction into a new address.
Winner #3 - Unannounced
The third winner of the auction exhibits some connection to the Cumberland Mining & Materials LLC of which very little is shown on their website. They have not announced their participation but it is believed by many individuals that watch the blockchain that they were the initial recipients.
 |
| Transactions to the third winner of the auction. |
The USMS initiated the transfer of the test 50 mBTC to the third winner about an hour after the last transaction, and then the USMS went home for the night. This left the bitcoin community in suspense overnight over how much the third winner would receive and wondering if there would be a fourth winner. But to their credit they were in the office super early the next morning to complete the transaction and sent the remaining balance to the third winner and thus wrapped up the auction before the markets opened on Tuesday. The third winner paid a transaction fee of 100 bits for both the test transaction as well as the final transaction, the only transaction fees paid in the third auction.
The reason why any information is known about this winner is because they used an address that had been used before on the blockchain and this address was also mentioned on twitter. Via some other internet detective work we can conclude that they have some connection to some other recognized names in the the exchange portion of the bitcoin ecosystem. But those details are outside the scope of this blog.
However it does not appear that Cumberland kept all of the bitcoin for themselves, it appeared they were acting as a syndicate for their bid.
 |
| Detail of three transactions from the third auction winner. |
Within three blocks transactions for 2K BTC, 14K BTC, and 5K BTC were peeled off of the awarded amount. The remaining sum of nearly 6K BTC was short the test transaction amount and the fees paid to receive the initial sum. Because of this I feel the 6K distribution remained with the administrator of the syndicate.
Nothing has been publicly stated about who the third winners were, nor who the members of the syndicate are. There is also the possibility that these are cold storage amounts for the same entity. However if it was cold storage I would have expected less movement of funds and more consistency in the size of the distributions. This is why I feel four entities joined into this syndicate.
PSA - Don't Reuses Bitcoin Addresses
I'de like to finish with a public service announcement: don't reuse your wallet addresses. Even the original paper on Bitcoin recognized the dangers of reusing addresses:
As an additional firewall, a new key pair should be used for each transaction to keep them from being linked to a common owner. Some linking is still unavoidable with multi-input transactions, which necessarily reveal that their inputs were owned by the same owner. The risk is that if the owner of a key is revealed, linking could reveal other transactions that belonged to the same owner.
[Section 10: Privacy, Bitcoin: A Peer-to-Peer Electronic Cash System]
Note that for the second winner we have never seen any of their addresses before. And the only reason we know anything about the third winner, their syndicate, and what they are doing with their transactions is because of a re-used address and a tweet associating that address to an identity.
I cannot stress enough how keeping addresses as single use entities is the simplest and most effort effective means there is to increase your bitcoin privacy.
Friday, February 20, 2015
Following the Inside Man
Last night (19 Feb 2015) Morgan Spurlock's show "Inside Man" premiered their episode about Bitcoin on CNN. Sure enough there were scenes of him paying for and receiving bitcoin. And since the transactions occured on the blockchain, they are available for proof.
The first bitcoins on his show is a small $0.25 gift for his brand new install of an Aegis Bitcoin Wallet he used for the whole show.
His next task was to buy a whole bitcoin at an exchange. After being inspired by Andreas Antonopoulos, he bought an entire bitcoin for $630 (this was filmed on 7 Jul 2014, so the price was good then).
Next he goes to upstate New York, but because of the magic of television editing we see him spending some of that hard bought bitcoin. First, he buys a pizza, or two. Thanks to the nice steady and straight on shot of the barcode we have a high level of confidence this is indeed the transaction where he bought pizza.
The blue transaction is when the pizza parlor cashes out their bitcoin (at a loss). Next he buys some groceries. And apparently they manage their bitcoins on the same address, because they also get cleared out in the same transaction.
Then after all that hard shopping and eating he gets a massage. Would you believe the massage place works off of the same vendor?
Actually, I'm not terribly sure about this one. Because in the video the transaction is stated as $20, and I cannot make out any QR codes nor is an exact BTC amount stated. But this is the closest one I can see. (Come on CNN, what's it going to take to get Inside Man filmed in 4K?) But it makes sense if they filed on one day and had only one vendor that needed to fill out a release. I'm sure they got a release just in case some snoopy person posts the transactions on some blog somewhere.
Next in the show we see a scene where Morgan "buys" airfare and hotel to the bitcoin mine he is about to visit. This is a bit of editing magic to provide a nice segue to the next segment. But the dates on the travel drop down start after the next transaction we will see. Furthermore, the two bitcoin addresses show zero transaction (which I won't link to as I don't want to encourage dust and tags to go there). But the point of the segment is that yes, you can book travel and hotels with bitcoin.
Now we go back in time to his visit where he worked briefly at a Bitcoin mine. He gets paid 0.3 BTC for his labors and gets to see a snazzy animation of his transaction showing up at blockchain.info.
Next he works with the (former) FBI agent who helped bring down the original Silk Road. Yea, we won't see him on the stand but he will do a CNN interview. (Makes you think the prosecution had a better strategy in mind than the defense.) Morgan then buys a "Fauxlex" from Silk Road 2. Except I doubt he used his Aegis wallet. You see, Morgan's wallet address seems to be 12qp1Ksm8NDxaermZpf4wbpdC2FSyupFx5, and all the outbound transactions I see coming from that address are either (a) too small or (b) go through Coinbase. I'de like to think that the Silk Road 2.0 operators aren't so dumb as to process transactions through Coinbase, but I've been wrong before.
Now after that late night on the deep web Morgan wakes up and is a little groggy, so he needs to get some coffee. He stumbles upon one vendor who will sell him coffee... for a $25 minimum charge. His complaint is that he loses money on the volatility if he goes too low. But this is really an educational opportunity because there are service providers (such as BitPay who had a banner at the Bitcoin center scene) who will immediately cash out your bitcoin to fiat at the time of your transaction. But Morgan has a large crew so buying 10 cups of coffee is actually a reasonable course of action.
Finally, he finishes the show at the Grumpy Cafe and recruits a new vendor to accept bitcoin. Although I don't think he has fully drank the Kool-aid on this one (being a coffee shop and all) since the payment is still sitting in the Unspent Transaction Outputs pool.
But what is interesting is what wasn't shown. By my reckoning Morgan also bought some bitcoin from Coinbase, and there were lots of vendors who used Coinbase to clear their transactions. Most of those transactions occurred off screen, and some of them were duplicates (like me I doubt Morgan can keep from going to the grocery store every day or two).
All in all I thought it was a fairly balanced piece on Bitcoin. It's not often you get a journalist to actually use bitcoin before reporting on it.
The first bitcoins on his show is a small $0.25 gift for his brand new install of an Aegis Bitcoin Wallet he used for the whole show.
His next task was to buy a whole bitcoin at an exchange. After being inspired by Andreas Antonopoulos, he bought an entire bitcoin for $630 (this was filmed on 7 Jul 2014, so the price was good then).
Next he goes to upstate New York, but because of the magic of television editing we see him spending some of that hard bought bitcoin. First, he buys a pizza, or two. Thanks to the nice steady and straight on shot of the barcode we have a high level of confidence this is indeed the transaction where he bought pizza.
The blue transaction is when the pizza parlor cashes out their bitcoin (at a loss). Next he buys some groceries. And apparently they manage their bitcoins on the same address, because they also get cleared out in the same transaction.
Actually, I'm not terribly sure about this one. Because in the video the transaction is stated as $20, and I cannot make out any QR codes nor is an exact BTC amount stated. But this is the closest one I can see. (Come on CNN, what's it going to take to get Inside Man filmed in 4K?) But it makes sense if they filed on one day and had only one vendor that needed to fill out a release. I'm sure they got a release just in case some snoopy person posts the transactions on some blog somewhere.
Next in the show we see a scene where Morgan "buys" airfare and hotel to the bitcoin mine he is about to visit. This is a bit of editing magic to provide a nice segue to the next segment. But the dates on the travel drop down start after the next transaction we will see. Furthermore, the two bitcoin addresses show zero transaction (which I won't link to as I don't want to encourage dust and tags to go there). But the point of the segment is that yes, you can book travel and hotels with bitcoin.
Now we go back in time to his visit where he worked briefly at a Bitcoin mine. He gets paid 0.3 BTC for his labors and gets to see a snazzy animation of his transaction showing up at blockchain.info.
Next he works with the (former) FBI agent who helped bring down the original Silk Road. Yea, we won't see him on the stand but he will do a CNN interview. (Makes you think the prosecution had a better strategy in mind than the defense.) Morgan then buys a "Fauxlex" from Silk Road 2. Except I doubt he used his Aegis wallet. You see, Morgan's wallet address seems to be 12qp1Ksm8NDxaermZpf4wbpdC2FSyupFx5, and all the outbound transactions I see coming from that address are either (a) too small or (b) go through Coinbase. I'de like to think that the Silk Road 2.0 operators aren't so dumb as to process transactions through Coinbase, but I've been wrong before.
Now after that late night on the deep web Morgan wakes up and is a little groggy, so he needs to get some coffee. He stumbles upon one vendor who will sell him coffee... for a $25 minimum charge. His complaint is that he loses money on the volatility if he goes too low. But this is really an educational opportunity because there are service providers (such as BitPay who had a banner at the Bitcoin center scene) who will immediately cash out your bitcoin to fiat at the time of your transaction. But Morgan has a large crew so buying 10 cups of coffee is actually a reasonable course of action.
Finally, he finishes the show at the Grumpy Cafe and recruits a new vendor to accept bitcoin. Although I don't think he has fully drank the Kool-aid on this one (being a coffee shop and all) since the payment is still sitting in the Unspent Transaction Outputs pool.
But what is interesting is what wasn't shown. By my reckoning Morgan also bought some bitcoin from Coinbase, and there were lots of vendors who used Coinbase to clear their transactions. Most of those transactions occurred off screen, and some of them were duplicates (like me I doubt Morgan can keep from going to the grocery store every day or two).
All in all I thought it was a fairly balanced piece on Bitcoin. It's not often you get a journalist to actually use bitcoin before reporting on it.
Subscribe to:
Posts (Atom)








