Enter the latest and most surreal twist in the Silk Road saga to date. Yesterday the DOJ released a criminal complaint against former DEA agent Carl Mark Force IV and former Secret Service Agent Shaun Bridges. The surreal part is not the core allegation, where it is alleged that Force and Bridges were skimming the profits from undercover drug sales. But where they had managed to embed themselves so deeply they were engaging in some of the more salacious stories emerging at the trial. The January 2013 theft? That was the undercover agents. One of the murder for hire allegations? Yep, complete with faked pictures. Causing the collapse of Mt. Gox? Well, no. I'm not convinced about it yet but it is at least in the realm of reasonable theories. Even Hollywood couldn't make this up. But remember, these are all allegations until proven in a court of law at trial.
I am not a Lawyer
I would like to point out that I am not a lawyer. I did not do any correspondence courses to the University of American Samoa and it didn't take me three tries to pass the State of New Mexico Bar Exam (I've never tried). So if you are reading this blog realize this is for entertainment purposes and is not legal advice. I feel the need to say this since I'm going to be re-creating some of the exhibits and pointing out a few minor clerical errors.
However what I do find significant in this complaint is that three of the exhibits showed a significant amount of blockchain analysis. This is something we didn't see in the Ross Ulbricht trial, the only connections entered into evidence were direct transactions between the Iceland server and Ross's laptop. But to be honest, that was really all they needed since the evidence was so overwhelming. This case is significant because they are entering in as evidence bitcoin traces involving multiple transactions. (And they even had a footnote on page 9 discussing the proper capitalization of bitcoin.)
Exhibit B
Exhibit B is the most complex graph in the complaint. It outlines a 525 BTC payment to Force received from DPR, where Force pretending to be a corrupt government official offering his knowledge and expertise (except allegedly he wasn't pretending). I was able to recreate this graph by entering only one of the addresses and waling up and down the transaction graph, so despite my nits the exhibit is generally correct.
 |
| Exhibit B [numisgraph] |
Compared to the Exhibit B graph (on page 55 of the PDF) there is one major stylistic difference is that I focus the vertices of the graphs in this blog on the transactions and the edges represent the transaction outputs that are attached to particular bitcoin addresses. The exhibit graph has the vertices as the transaction outputs. In fact, some vertices represent multiple transactions that are self spending peeling transactions. The flaw I see in this is that there is no room for the transaction IDs and some details about the creation and spending of transaction outputs can be lost.
There are also a few clerical errors in the exhibit in the complaint, and some elided details that exist in the transactions that are lacking in an address focused graph. This is likely the result of copy paste errors as it appears that a tool such as PowerPoint or Analyst's Notebook was used to generate the exhibit. The left two branches from DPR have the second and third addresses swapped. There are some coins that exit the system just to the lower right of the center of the exhibit. Those coins do exit but there are several intervening addresses left out of the exhibit. And the major sweep at the bottom of the graph is actually two sweeps from two different addresses, all winding up in the 136jvwh address eventually.
There are advantages of a hand made graph. The lines and arrangement of the graph are much more aesthetically pleasing. Right now I am using JGraph for my graphing layout but I am exploring a more expensive option, but based on my professional experience yFiles is the best library in the business for graph layouts. You also pay for the quality of the work.
All these nits aside the core narrative of the exhibit is correct: DPR danced 525 bitcoins to Force in a complex series of transactions. The clerical errors and stylistic nits do nothing to diminish this message.
Exhibit E
Exhibit E represents the payment of 770 BTC from DPR to Force (under the pseudonym frenchmaid) in connection with the alleged murder for hire that Force lied about carrying out.
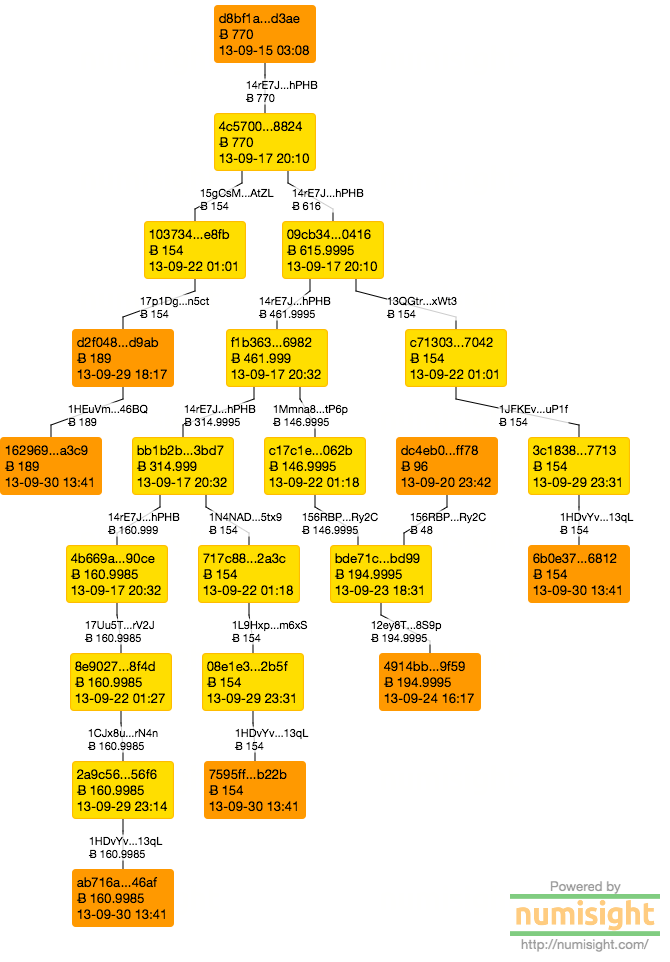 |
| Exhibit E [numisgraph] |
Exhibit F
This exhibit is even less interesting than Exhibit E was compared to Exhibit B. It represents the skimming done by Bridges into Mt. Gox, and then to his Fidelity account.
 |
| Exhibit F [numisgraph] |
Conclusion
This will be an interesting case to watch as it winds its way to trial. Whereas the Ross Ulbricht case relied on simple single transactions this case depends on a more complex series of blockchain transactions to prove the allegations against Carl Mark Force IV. When it comes to entering information in as evidence this is likely a case that will be sited in much of the case law that will develop.
You also may have noticed the "numisgraph" links in the captions. If you want to play along at home you can download the public alpha of the Numisight Bitcoin Explorer and load the attached files and explore the related transactions yourself.




